Computer Networking Lecture Notes
11 March 2013 • Wireless Medium Access
Outline
- Wireless
- Propagation
- Reservation
- IEEE 802.11, Wi-Fi.
- Topologies and architecture
- Frames
Shared Channels
- Shared (multiaccess, broadcast, random access) channels.
- What’s so special about wireless channels?
- Why haven’t we solved this problem already?
Wireless Properties
- Three important wireless properties:
- Half duplex operation; a host can send or receive, not both.
- A time varying, complex channel.
- Frequent (1 in 103 BER) and bursty errors.
- A wired connection is full duplex, consistent and simple, and exhibits low, random errors.
- Wireless MAC protocols are correspondingly more complicated.
Propagation
- Assume radio signals propagate uniformly in all directions.
- Not even close to being true.
- Eventually signals become too weak to receive (fade).
- Distance squared drop-off.
|
|
|
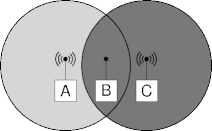
Hidden Senders
- Both A and C want to send to B.
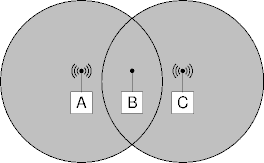
- The hidden sender problem.
Good-Bye CSMA/CD
- Half-duplex transmission eliminates collision detection (CD).
- No listening while sending.
- Carrier sense (CSMA) is still possible.
- But hidden senders reduce its effectiveness.
- This is not the propagation-delay collision window problem.
- Although that problem exists too.
Exposed Senders
- A wants to send to B, C wants to send to D.
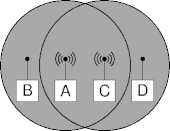
- The exposed sender problem.
- Also the discontinuous LAN problem.
Capture
- A and C sending to B, C’s signal is stronger
than A’s signal.
- C captures B.
- Sometimes capture is a problem, sometimes it’s a feature.
Other Factors
- Mobility and power are two more important factors.
- No wired tether leads to hosts that can move.
- Network boundaries are not human friendly.
- Mobile devices tend to be small, and small batteries are not power
dense.
- Radio I-O requires power.
ALOHA
- What about ALOHA?
- Pure ALOHA is a simple fully distributed algorithm.
- Slotted ALOHA too, but less so.
- However, even under modest contention ALOHA isn’t efficient.
- And it degrades rapidly under load.
- Collisions are expensive in a mobile wireless environment.
Wireless MAC Protocols
- Particular services and infrastructure need particular MAC protocols.
- Bluetooth (IEEE 802.15) - personal-area networks (PANs).
- Wi-Fi (IEEE 802.11) - local-area networks (LANs).
- WiMax (IEEE 802.16) - metropolitan area networks (MANs), wireless last miles.
- Other contenders include radio-frequency ID (RFID) and Iridium-like satellite networks.
Wi-Fi Protocols
- Some of the Wi-Fi IEEE 802.11 standards.
802.11 GHz Mbit/sec* original 1997 2.4 2 a 1999 5 54 b 1999 2.4 11 g 2003 2.4 54 n 2009 2.4 or 5 600 - *Maximum; actual bit rates vary adaptively.
- Development continues.
Wi-Fi CSMA
- Carrier sense can be helpful, but avoiding collisions is even more helpful.
- Non-slotted p-persistent CSMA provides the starting point.
- Don’t flip a coin on an idle channel, randomly backoff.
- No collision detection, so expect acknowledgments.
- This is known as multiple access collision avoidance (MACA, also CSMA/CA).
CSMA/CA
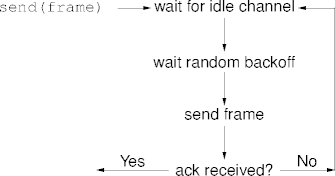
- Backoff time is adjusted to channel characteristics.
Reservation
- Carrier sense is helpful, and reservation is even more helpful.
- Use small frames to reserve clear channels around sender and
receiver.
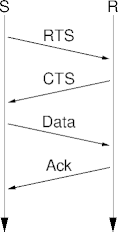
- Sender emits ready to send (RTS).
- Receiver emits clear to send (CTS).
- Data follows.
- RTS-CTS reservation is an optional CSMA/CA feature.
CSMA/CA Reservation
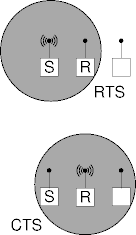
- RTS and CTS frames are small (10s bytes).
- Less likely to collide, less lost when they do.
- Sender’s and receiver’s neighbors hear the reservation frames and mute to avoid collisions.
- RTS and CTS contain expected channel hold time.
- Neighbors compute the mute-period size.
CSMA/CA Example
|
|
|
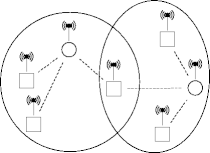
802.11 Topologies
- A collection of communicating systems is a basic
service set (BSS)
BSS Independent BSS 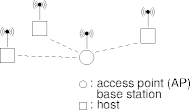
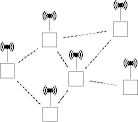
Basic Service Systems
- An independent BSS is also known as an ad-hoc or mesh
network.
- Hosts communicate directly (or indirectly) with each other.
- All communication in a BSS goes through a distinguished system called
the access point or base station.
- All communication not with the access point is indirect.
802.11 Architecture
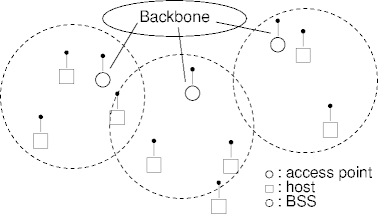
- Now imagine the hosts moving around.
Distribution Systems
- Two or more BSSs can be connected via a
distribution system (DS) or a backbone.
- The backbone is not part of 802.11, although it could be wireless.
- The backbone can be connected to other networks too (the Internet, for example).
- An infrastructure is a collection of BSSs interconnected with distribution systems.
Finding APs
- A host scans for an access point:
- Host broadcasts a Probe frame.
- APs reply with a Probe Response frame.
- Host chooses an AP and sends an Association Request frame.
- The AP replies with an Association Response frame.
- A host scans for an AP when it doesn’t have one, or it wants a better one.
Scanning
- Host initiated scanning is called active scanning.
- Access points also provide passive scanning.
- APs periodically broadcast Beacon frames.
- A Beacon frame advertises an AP and its capabilities.
- A hand-off occurs when a host changes APs.
802.11 Frames
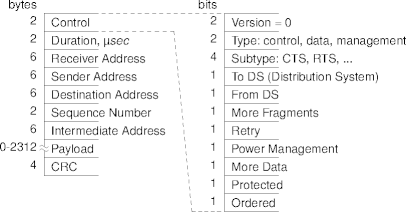
Other Wi-Fi Protocols
- There are a number of other Wi-Fi protocols in place or under
development:
- 802.11e - Quality of service specifications.
- 802.11i - Security enhancements (replacing WEP).
- 802.11k - Access-point selection.
- 802.11r - Mobile management and hand-off.
- 802.11s - Mesh (ad hoc) networks.
Bluetooth
- Bluetooth, a wireless technology to replace data cabling.
- Also a 10th century Danish king.
- An example of a personal-area network (PAN).
- Distance usually between 1 and 10 m.
- Data rates between 1 and 3 Mbit/sec.
- Developed by an industrial consortium.
- Standardized by IEEE 802.15.
Bluetooth Frequencies
- Bluetooth operates in an unlicensed ISM band from 2.4 to 2.4853 GHz.
- Which conflicts with the lower Wi-Fi frequency band.
- The band is divided into 79 1 MHz channels and two approximately 2 MHz guard bands.
- The Bluetooth physical layer uses frequency hopping spread spectrum.
- A form of frequency-division multiplexing.
Bluetooth Architectures
- All hosts are mobile.
| Piconet | Scatternet | |
|
|
Masters and Slaves
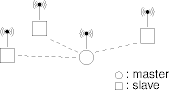
- A Bluetooth host discovers nearby hosts and pages responders
to form a piconet.
- The discoverer is the piconet master, the responders are the slaves.
- A master has up to seven active slaves, and any number of
parked slaves.
- The master activates and parks slaves as necessary.
- Slaves can request master status.
Scatternets
- A host in more than one piconet is a bridge host.
- The bridge is a master in at most one piconet.
- A bridge time-division multipexes among piconets.
- A group of hosts can form several piconets to get a scatternet.
- This approximates peer-to-peer communication among hosts.
WiMAX
- WiMAX (Worldwide Interoperability for Microwave Access).
- An example of a metropolitan-area network (MAN).
- Distance up to 10-30 miles.
- Data rates between 30 and 40 Mbit/sec.
- A set of IEEE 802.16 standards.
Summary
- Carrier sense is less of an advantage for wireless.
- And direct collision detection is impossible.
- IEEE 802.11 (Wi-Fi) is one of many wireless specifications.
- Others include Bluetooth, WiMax, and G3-G4-LTE.
- There are many 802.11 specs, and more are on the way.
| This page last modified on 2011 October 9. |