Computer Networking Lecture Notes
28 January 2013 • Computer Networking
Outline
- Networks.
- Network architecture and protocol software.
- Measuring networks.
- Network security.
Networks
- Why networks?
- To move bits from one system to another.
- For what purpose?
- To communicate, mostly.
- Communicate what?
- It doesn't matter (to a first approximation).
- But it does matter, somewhat.
- The more you know, the better you can do.
Networked Systems
- A network is a bit pipe connecting systems A and B.
- More generally, a network connects any two systems with a bit pipe.
- A complete network.
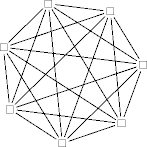
- More generally, a network connects any two systems with a bit pipe.

Network Structure
- For various reasons, a complete network is a useful model but a terrible implementation.
-
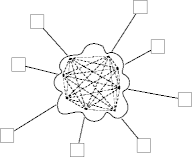
- Abstract the useful behavior, hiding the unhelpful structure.
- Our goal is to design and build this network cloud.
Communicating Bits
- Two end-points require common knowledge to communicate.
- Recognize the words used, structure or syntax.
- Understand the words used, meaning or semantics.
- A pre-arranged (pre-communicated) understanding between end-points.
- Otherwise communication is difficult and ineffectual.
Protocols
- A protocol is the pre-arranged understanding between end-points.
- A protocol defines the syntax and semantics of communication.
- The form and meaning of communication.
- Protocols define and instruct network behavior.
- Necessary for the network user and the network designer-implementer.
Complexity
- Networks are complex, difficult environments.
- Protocols describe complex, difficult behavior.
- The combination of environment and behavior can be overwhelming.
- Impose structure on the network and protocols to control complexity and
difficulty.
- Hardware network structure.
- Software protocol structure.
Layering
- Layering is a way to controlling complexity.
- A complex system is broken up into simpler layers.
-
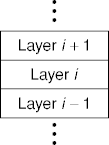
- Each layer implements a slightly more complicated system using the slightly simpler system implemented by the next lower layer.
- The highest layer implements the desired system.
Layered Services
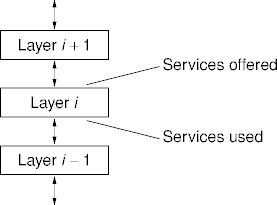
Example Protocol Stack
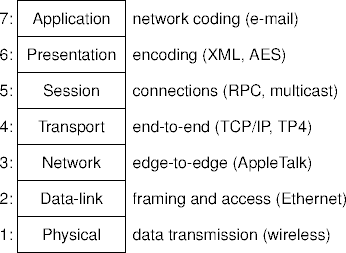
The ISO OSI Protocol Stack
- The International Standards Organization (ISO) standardizes lots of things, including networks.
- The ISO defined the Open Systems Interconnection (OSI)
model to clarify network function.
- The seven-layer model.
- The ISO OSI stack is a conceptual model, not a reference implementation.
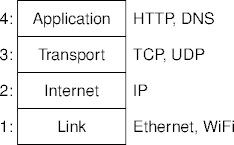
Another Example
- This is the Internet Protocol (IP) model.
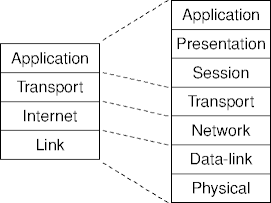
Stack Relations
Network Performance
- There are many measures of network performance:
- Throughput - Sustained bits/time to the receiver.
- Latency - Time to receive the first bit.
- Delay - Time to receive the last bit.
- Goodput - TransferSize/Latency (scaled by overhead).
- Jitter - Variation in latency.
Network Ranges
- Computer networks can be classified by the span they cover:
- Personal-area networks (1-2 meters, Bluetooth).
- Local-area networks (1 km, WiFi).
- Metropolitan-area networks (10 km, Cable).
- Wide-area network (1000 km, NSFNet).
- The Internet (10,000 km).
Scaling
- Scaling characterizes how a system changes when size changes.
- How an ecosystem changes with increasing animal population.
- How a mutual fund changes with increasing investor dollars.
- How a network changes with increasing hosts.
- Scale-related change is described with asymptotic (big O) notation.
Scaling Networks
- Scaling fully-connected point-to-point networks to n hosts requires O(n2) links.
- Dedicated switching fabrics can scale subquadratically.
- The nodes in the fabric are called switches or routers.
Network Security
- Three concerns:
- Attack — what happens to the network?
- Defense — what are the counter measures?
- Protocol security — do protocols hinder or help security?
- There are other security concerns.
- Physical security; social engineering.
Assumptions
- The assumptions underlying security definitions are crucial.
- Assume Eve (trad., short for eavesdropper)
- sees everything on the network.
- can modify and interfere with network traffic at will.
- Make sure you understand the assumptions behind security claims.
- For example, Microsoft NT and C2 certification.
Consequences
- Ordering from an on-line store serving plain-text information:
- Eve sees the order, gathers customer information, steals identity.
- Using telnet (plain-text communication):
- Eve injects her commands into the stream.
- Updating software.
- Eve changes the vendor’s updates to hers.
Threat Types
- An adversary can violate
- secrecy assumptions (steal passwords, credit-card numbers),
- traffic integrity (modify shipping addresses, site spoofing),
- service availability (denial of service attacks).
- The collected set of danger points is called the attack surface.
Possible Solutions
- Security is based on obscuring information.
- Not on obscuring security techniques.
- Cryptography (encryption-decryption) is the principle obscuring
mechanism.
- There are others (needle-in-haystack protections).
- What are the assumptions under which cryptography is a suitable solution to security problems?
Solution Examples
- Cryptographic algorithms are the basis for other approaches to
protection.
- Authentication protocols (Kerberos).
- Message Integrity Protocols (SHA1 message digests).
- Key distribution (SPKI, a hard problem).
Summary
- Networks link interesting places to allow interaction.
- Protocols determine the rules of interaction.
- Protocol layering combats network complexity through structuring.
- Security maintains desirable characteristics for interactions.
References
- The Structure of the “THE”-Multiprogramming System by Edsger Dikjstra in Communications of the ACM, May, 1968.
| This page last modified on 2012 September 6. |
