Computer Networking Lecture Notes
2013 December • Introduction
Course Description
- A computer networks course.
- Inside the network, mostly.
- Upper level, software-oriented view.
- Concepts and implementation, abstractly.
- Co-reqs:
- Officially: foundations, 502.
- Unofficially: operating systems, 505; programming (501A, 501B, 503).
Classes
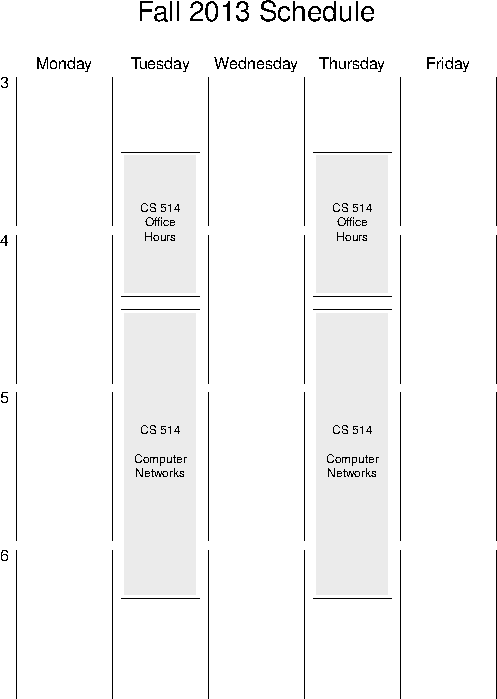
- Classes meet Tuesdays and Thursdays, 4:30 to 6:20 in HH 316.
|
|
|
Schedule
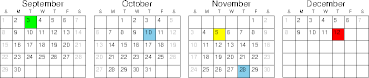
- No classes on Thursday, 10 October, and Thursday, 28 November.
- Drop day Tuesday, 5 November.
- Last day Thursday, 12 December.
Objectives
- Learn networking basics: purpose, mechanism, and design.
- The major network layers and their interactions.
- High-level understanding of network services at all layers.
- Basic implementation details.
- Maintain your balance on uneven and rapidly changing terrain.
Example
Dan Kusnetzky, Program Vice President for System Software at IDC, makes the following illustrative comparison. “If I was trying to get forty tons of gravel from New Jersey across the Hudson river to New York City, I could use one truck and fight traffic and the lines at the toll booth to move it in. Or, I could divide it into 40 1-ton loads, give the drivers radios to communicate, and they can get there faster, because they’re more agile and can find the most efficient route.”
Enterprise Grid Computing, Clay Andres
Linux Magazine, October 2004
Instructor
- Richard Clayton, HH 318 (the adjunct’s office).
-
rclayton@monmouth.edu
-
- Office hours Tuesdays and Thursdays, 3:30 to 4:25, in HH 318.
- Make an appointment for other times.
Grading
- Grading comes from tests and homework assignments.
- Three tests, roughly one a month.
- Eight homework assignments, one per two-week section.
- No other grade sources: not attendance, not class participation, not
…
- In particular, no mid-term or final exams.
Final Grade
- The final grade is the straight, unweighted average of the nine highest
test and homework grades.
- Three tests and six homework grades.
- The lowest two homework grades are dropped.
- No grades are scaled to a curve.
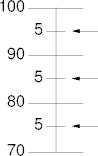
Final Grades Example
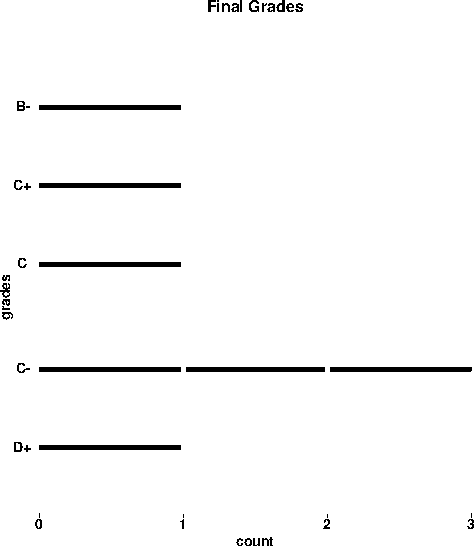
Grade Ranges
- The usual grade ranges are in effect:
95 ≤ A 90 ≤ A- < 95 86.6 ≤ B+ < 90 83.3 ≤ B < 86.6 80 ≤ B- < 83.3 76.6 ≤ C+ < 80 73.3 ≤ C < 76.6 70 ≤ C- < 73.3 F < 70
Grade Interpretation.
- The grade meanings in this class:
A: The answer is right. B: The answer is almost right. C: Nice try. - These interpretations hold for everything: homework, tests, final grades.
A-Level Answer Example
Q: Public-key cryptography or symmetric cryptography can be used for authentication. Which is the more practical for authentication? Justify your answer.
A: Public-key authenticating is more practical. The identifying secret in public-key cryptography remains secret. Symmetric-key authentication requires distributing the secret to all those requesting authentication.
B-Level Answer Example
Q: Public-key cryptography or symmetric cryptography can be used for authentication. Which is the more practical for authentication? Justify your answer.
A: Public-key cryptography is more practical. It is more practical because public key uses a different key for encryption and decryption whereas symmetric key uses the same key for both, making it easier to crack.
C-Level Answer Example
Q: Public-key cryptography or symmetric cryptography can be used for authentication. Which is the more practical for authentication? Justify your answer.
A: Public key is less private than symmetric key. The keys are available to the world. Symmetric key uses simple mechanics to encrypt the data. Since authentication requires heavy security (typically), it should be as private as possible.
Grade Interpretation..
- Grades start at the 5s: 95 or 85.
- Grades move up and down from 5 based on qualities.
- Clear and concise answers.
- Work required to understand.
|
|
|
Textbook
- There is a textbook for this class.
- Pick your own textbook.
- But make sure you have at least one.
- There is a textbook for this class.
- Compare table of contents and index against the syllabus.
- See the bibliography for recommendations.
- Make sure your e-mail works, and you know how to work it.
- The class e-mail address is
- censored.
- Mail goes to everybody in the class.
E-Mail Archive
- E-mail is stored in a web-accessible hyper-mail archive.
- E-mail to the mailing list is added to the archive.
- E-mail to me is also added if of general interest.
- Unless requested not to.
Home Page
- The class home page is
-
www.monmouth.edu/~rclayton/web-pages/f13-514/index.html - Or
tinyurl.com/mucs514f13h(note the ‘h’).
-
- The lecture schedule is
-
www.monmouth.edu/~rclayton/web-pages/f13-514/schedule.html - Or
tinyurl.com/mucs514f13s(note the ‘s’).
-
Screencasts
- Lectures will recorded and be made available at the Vimeo CS 514
screencast channel.

Downloading
Microblogging
- Follow mucs514 on Twitter.ca.
-
Assistance
- See me if you need special assistance.
- If you know what I’m talking about, you know what to do.
- If you don’t know what I’m talking about, it doesn’t matter.
Attendance
- I have no attendance policy for lectures; you may attend them or not.
- However, you are responsible for everything that goes on during lectures.
- I expect good attendance for other parts of the course, tests in
particular.
- Repeated violations I have to attend to will put me in an uncharitable mood.
Cheating
- I don’t care how you put knowledge in your head.
- But I do care that knowledge comes out of your head.
- Cheating is not doing your own work.
- Copying assignments, copying test answers is cheating.
- Cut ‘n’ paste research on the Web is cheating.
Adjudication
- The mechanism for dealing with cheating is:
- Give everybody zeros.
- Judge mitigating evidence and adjust accordingly.
- Elevate for further adjudication.
- Step 2 is the tricky one.
- It’s gotten progressively brutish and short over the years.
Working Together
- Paradoxically, I recommend working together.
- On assignments, and studying, not on tests.
- To avoid problems, only make copies inside your head.
- a.k.a. learning.
Grade Complaints
- I encourage students to question their grades.
- But
- I only argue about answers.
- You have a limited time to raise questions.
- Make sure you understand my answers.
Late Assignments
- Don’t hand in assignments late.
- Late penalties are steep.
- You’re not going to be able to climb out of the hole.
- Falling behind in assignments is generally a bad idea.
- It’s double bad for linked assignments.
Missing Tests
- Let me know if you’re going to miss a test.
- You can schedule a make-up at your convenience.
- Unexcused absences are handled more severely.
- The tests are harder.
- The scheduling is much harder.
| This page last modified on 2013 September 1. |