Computer Networking Lecture Notes
2013 September 19 • Application Security
Outline
- Application security
- Protection mechanisms.
- Cryptography
- Breaking cryptography.
- Symmetric- and asymmetric-key cryptography.
- Identity: authentication and verification.
Application Security
- What is application security?
- Move data from sender to receiver securely.
- “Securely” means whatever you want.
- Private — only the sender and receiver understand the data.
- Inviolate — the data sent is the data received.
- Certain — Each side knows the other side is involved.
Security Attacks
- The definition of security is the security policy.
- Mix ‘n’ match to make your own policy.
- The attacks against security policies are legion.
- Privacy — eavesdropping.
- Inviolate — replay.
- Certain — relay (man in the middle), spoofing.
Protection Mechanisms
- Security attacks outnumber protective mechanisms.
- Privacy — encryption.
- Inviolate — checksumming, message digests.
- Certainty — digital signatures.
- Attacks are broad-based and diffuse.
- Protections are more powerful but have limited scope.
Cryptography
- Cryptography is a fundamental data transformation in security.
- A cryptographic algorithm (a cypher) obscures (encrypts) data relative to a secret (a key).
- The algorithm (or a related one) also unobscures (decrypts) the obscure data relative to the secret (or a related one).
- Encrypting or decrypting data without the secret should be impossible.
Cypher Example
- The Ceasar cypher shifts letters in an alphabet A by integer k.
- Encryption: Ci → C(i + k) mod |A|.
- Decryption: Ci → C(i - k) mod |A|.
- Key: k
- Example:
- if k = 5, cow encrypts to htb.
- if k = 4, htb decrypts to dpx.
Cryptographic Security
- A secure cypher is impossible to decrypt without the key.
- There’s one mathematically proven secure cypher: the one-time pad cypher.
- All other cyphers may be secure.
- Security comes from the computational complexity of decrypting without a key.
- This is fragile, technology-dependent security.
- R.I.P. DES.
Breaking Cryptography
- A cryptographic algorithm is broken when cyphertext can be
decrypted without a key.
- Or the key can be recovered from the cypertext (WiFi security).
- Practically, quasi-security comes from the difficulty of breaking
cyphers.
- A message with a useful life of X years should be protected by a cypher that takes at least X years to break.
- A common, but dangerous, interpretation.
Symmetric-Key Cryptography
- A symmetric-key cypher uses the same key for encryption and
decryption.
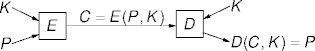
E:Encryption algorithm
D:Decryption algorithm
K:Key
P:Plaintext (data)
C:Cyphertext
Asymmetric-Key Cryptography
- An asymmetric-key cypher uses different but related keys for
encryption and decryption.
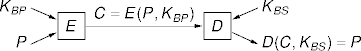
E:Encryption algorithm
D:Decryption algorithm
KBP:Bob’s public key
KBS:Bob’s secret key
P:Plaintext (data)
C:Cyphertext
Cryptographic Techniques
- Cryptographic algorithms combine character substitution and transposition techniques.
- Substitution: plaintext characters are mapped to other
plaintext characters.
- The Caesar cypher.
- Transposition: permute a plaintext character sequence.
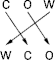
- Most modern cyphers: DES, AES, …
Problem Solved?
- Are we done? Does good cryptography provide security?
- Unfortunately, no.
- Generating good keys is hard.
- Good keys are inconvenient to handle.
- Distributing keys is hard and expensive.
- Cryptography is ineffective for other common attack points.
- Physical security, social engineering, …
Authentication
- The authentication problem: how does Alice know the message is from Bob?
- One possible solution is:
- Alice knows only Bob knows secret k.
- If X can prove to Alice it knows k, then
- Alice knows X is Bob.
- The cryptographic algorithm acts as a digital signature.
- Can the solution be implemented?
Asymmetric-Key Authentication
- Suppose Bob’s secret is KBS, his secret key.
- Alice challenges X with C = E(P, KBP).
- X responds with P\('\).
- If P\('\) = P, then P\('\) = D(C, KBS) and X is Bob.
- If P\('\) \({}\ne\{}) P, then X is still unauthenticated.
- This is the basic idea; there are lots of details to fill in.
- Problem solved?
Attack!
- Oh no:
- Alice is made to think that Bob knows KES, Eve’s secret key.
- Alice authenticates Eve as Bob.
- Poor Alice.
- Alice needs a way to reject the false claim that Bob knows a secret when he doesn’t.
- How can Alice do this?
Verifying Identity
- A verified digital signature only proves that X knows a secret.
- It doesn’t prove (or establish) that X is Bob.
- Alice doesn’t know, and Eve’s going to lie.
- A third party needs to establish to Alice that
if X knows k, then X is Bob.
- How does that go?
Identity Verification
- Introducing Vera, a trusted, independent third party.
- Bob verifies his identity to Vera, gives her a public key.
- Vera creates a digital certificate for Bob.
- Alice asks Vera about this Bob character.
- Vera sends Alice Bob’s digital certificate.
Digital Certificates
- A digital certificate can contain lots of information, but it must
contain
- Bob’s public key, and
- Vera’s digital signature.
- Does this solve the problem?
- Not really, but
- It’s (presumably) harder for Eve to masquerade as Vera.
- X.509 is a ITU-T digital-certificate standard.
SSH Example
- Secure Shell (SSH) is a remote log-in service replacing
telnetandrlogin. - SSH provides authentication, integrity, and privacy.
- SSH v. 2 uses three protocols for security policy: SSH-TRANS, SSH-AUTH, and SSH-CON.
SSH Transport
- SSH-Trans is a transport (end-to-end) service providing an encrypted channel.
- The underlying connection is a byte-stream (TCP).
- The SSH-Trans protocol:
- The client opens a byte-stream to the server.
- The client authenticates the server.
- They establish a session key to encrypt data over the stream.
Server Authentication
- What gives the client the server’s public key?
- The server:
we ssh opus 'opus (10.1.13.154)' authenticity can’t be established. RSA key fingerprint is d0:4e:70:f0:db:2a:dd:77:8b:67:a2:cd:0e:0f:3a:26. Do you want to continue (yes/no)? yes Added 'opus' (RSA) to known-hosts list. Last login: Sun Aug 19 13:06:26 2012 from rockhopper op
-
sshremembers the key if accepted.op exit Connection to opus.monmouth.edu closed. we ssh opus Last login: Thu Sep 20 18:20:16 2012 from westrunton op
SSH Connections
- SSH security services are so useful they’ve been packaged for use by
other applications.
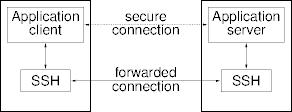
- This technique is called tunneling.
Summary
- Security is a game; make sure you understand the rules.
- Cryptography in one form or another is a basic security tool.
- But there are many security threats it doesn’t address.
- Claiming and establishing identity is an important operation in secure
systems.
- And the current identity infrastructure is rickety.
| This page last modified on 2012 September 20. |
