- Hash table ADT.
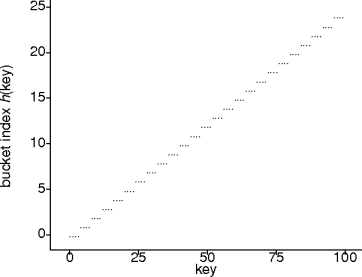
- Hash functions.
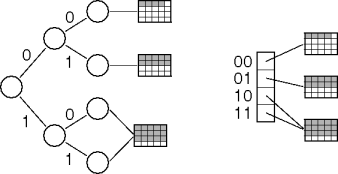
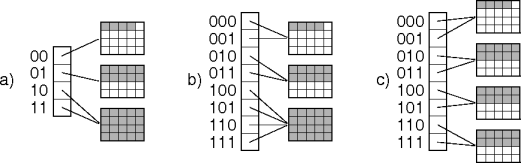
- Scatter tables.
- Open addressing.
- Chaining
- Dynamic hash tables.

|

|
add(), delete(), and
find().
void add(key k)
linked-list chain = table[hash(k)]
if not chain.member(k)
chain.add(k)
void delete(key k)
linked-list chain = table[hash(k)]
if chain.member(k)
chain.delete(k)
bool find(key k)
return table[hash(k)].member(k)
|
|
add(), delete(), and find() use the locate() private operation.
bool locate(key k, int & hi) hi = hash(k) step = 1 or i2 or hash2(k) for i = 1 to B if not in-cluster[hi] return false if occupied[hi] and table[hi] == k return true hi = (hi + step) mod B hi = -1 return false
void add(key k) if not locate(k, hi) if hi > -1 table[hi] = k occupied[hi] = true in-cluster[hi] = true void delete(key k) if locate(k, hi) occupied[hi] = false in-cluster[hi] = in-cluster[hi + 1 mod B] and in-cluster[hi - 1 mod B] bool find(key k) return locate(k, hi)
rp[], a
random permutation
of the 256 integers 0 to 255 (byte values).
v[] of n byte values, hash v into a
byte value h with
byte hash(byte v[], unsigned n)
byte h = rp[v[0]]
for i = 1 to n - 1
h = h xor rp[v[i]]
return h
hash() produces multi-byte hash values.
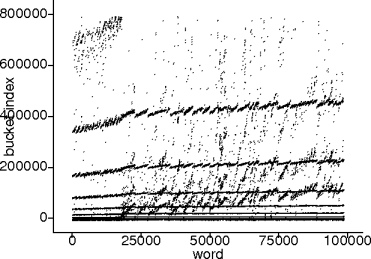
unsigned hash(unsigned k) return k mod B
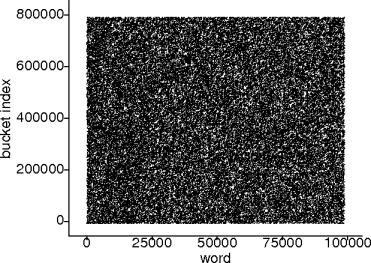
unsigned hash(unsigned k) return (M*k + a) mod B
unsigned hash(unsigned k) return floor(B*fraction(k*A))
XOR 0 1 0 0 1 1 1 0
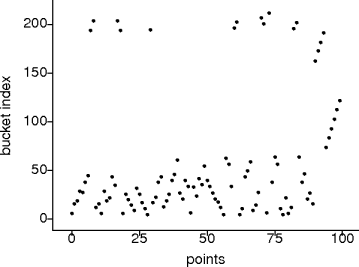
(x*101 ^ y*97) % B.
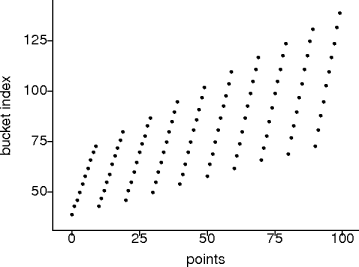
(round(x*101)*round(y*97))/256 % B.
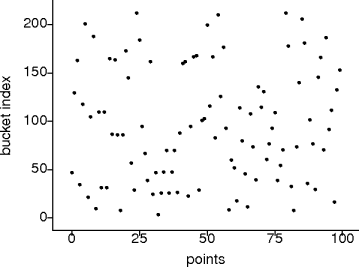
(round(x*101)*round(y*97))/2 % B.
unsigned point::random(double k) return (M*static_cast<int>(k*11) + a) % s unsigned point::hash() return random(x)*random(y); template <typename T> unsigned hash_table(const T & e) return e.hash() % size
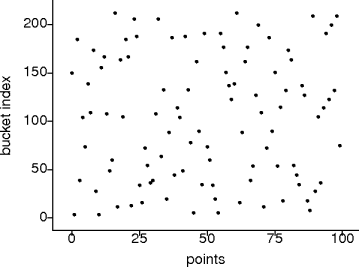
M = 25173, a = 13849, s = 65536.
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|